admin/ marzo 29, 2021/ Uncategorized/ 0 comentarios
¿Habra pacto con los Ransomware?
2020 was characterized by the leading role technology played in all sectors.
Ransomware continues the trend of targeted attacks but with the added challenge of double extortion. Organizations need to be one step ahead of such coercive tactics to avoid potential disruptions, financial losses, and reputational damage.
A ransomware infection can put organizations in difficult situations. The damage that WannaCry and Petya have caused has made people more wary, leading to stricter and more consistent security measures against a constant threat. Developments in ransomware over the past year have made dealing with ransomware not only difficult but also a delicate matter. Aside from the continuing trend of big-game or targeted attacks, ransomware operators have also come to rely on the cost of data breaches and double extortion to corner their victims into complying with their demands.

We have to accept that. 2021 will be a year that will still demand much from us. Fortunately, there is also no denying that we will have a no lesser advantage: the jolt – social, economic, cultural, scientific – that gave us 2020 with the Covid-19 pandemic has left us good lessons, also in cybersecurity. If we take advantage of these teachings, the next 12 months, despite the applicants circumstances, will not be an impossible way to walk.
In the case of the cybersecurity of organizations, the learnings of the year that is about to end are especially valuable, as they point out trends and contexts (several created by or enhanced by the health crisis), which should be considered in digital protection initiatives by 2021. Then six factors that no Mexican company, particularly its technology and computer security leaders, should go high.
It’s essential to understand how the current versions of ransomware came about so that organizations can learn to steer clear of such traps. Using case studies and examples, we examine the ransomware variants that populated 2020 in hopes of creating a guide for dealing with future attacks.

Evolution of ransomware
When ransomware created a niche for itself in the cyberthreat landscape, it was categorized as scareware, similar to FAKEAVs that used fake scan results to frighten victims into paying for bogus antivirus software. Slowly, more successful ransomware families progressed into something more threatening as they began to encrypt files. But even these tactics lost their edge over time. Organizations adapted. People realized that simple security measures like regular backup practices can significantly reduce a ransomware attack’s damage. In addition, ransomware actors had a “shotgun” approach (indiscriminately distributing their malware) that allowed antivirus providers to develop solutions to defend against them. In a sense, ransomware notoriety diminished from a hazard to a nuisance. Unfortunately, this was only temporary.
Can your business afford the following?
- Stop or delay your operations due to a cyber attack??
- Allow your information to be used by cyber criminals?
- Pay ransom to regain control of servers and computers?
- Allow your company’s computer network to be infected with viruses and malware?
Above all
- Do you know what your tech system weaknesses are and how to solve them?
- Is your company updating the protections for your computer network every day?
- Does your business have the staff, time, and technology to solve these problems?

If the answer to any of the above questions is no, then your business is the right candidate for the next cyber attack.
Please find below our self-evaluation tool that will allow you to identify your cybersecurity vulnerabilities. We can help you build your cybersecurity roadmap.
*If you want to download the full infographic document, please follow the link below and fill the form with your information*
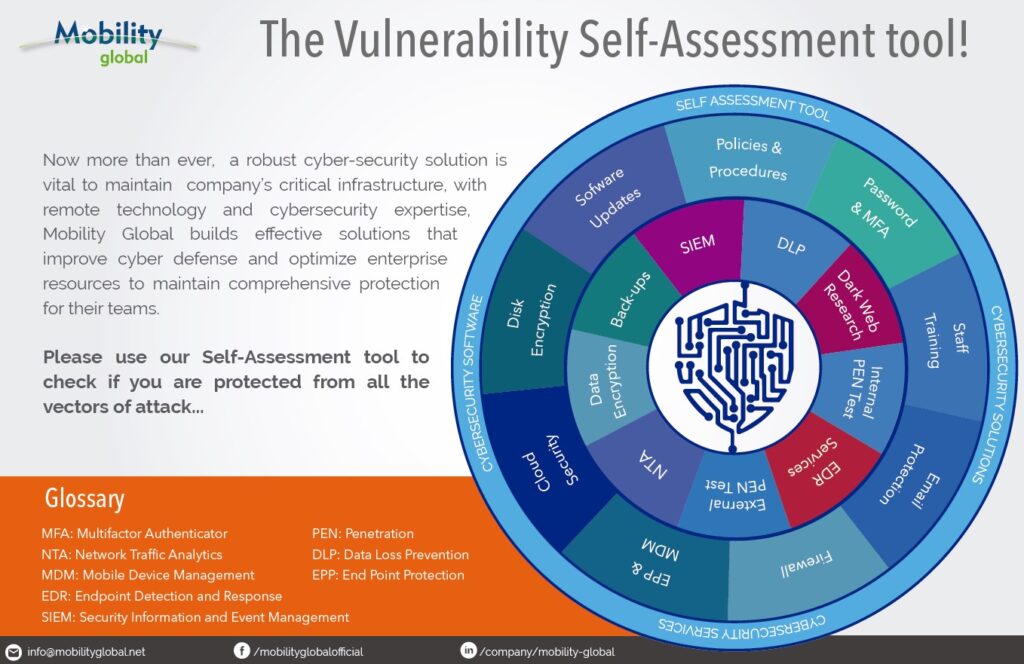
Are cyber security threats increasing?
Yes, threats are increasing exponentially in sophistication, intensity, diversity, and volume. Cyber experts report significant escalation in external cyber attacks, especially from criminal organizations and foreign state-sponsored activities.
Do mobile devices present security risks?
Mobile devices do bring great utility in terms of convenience and allowing individuals to be «online all the time.» Governments have widely deployed mobile devices for accessing resources and greater workforce productivity. However, using mobile devices to communicate and share data creates inherent security issues and adds more points of access to the network. Mobile malware threats are indeed growing, and a significant security concern with mobile devices is the device’s loss.
What capabilities are necessary components of a cyber security strategy?
Traditional approaches focused on preventive and risk-based protective measures. Risk-based meaning that the investment in security is a function of the perceived value of the protected information. Those approaches continue to be the necessary aspects of security. However, any more state government must include two additional capabilities: vigilance and resilience.
Vigilance is continuous monitoring for threats that give early detection. Resilience is the ability to respond and recover. These capabilities must be continually enhanced to anticipate the growing threat landscape.
How significant is privacy as a component of cyber security?
Very significant. There has been an unprecedented growth of social media, personal cloud services, and employees utilizing personal devices and third-party applications. This parallels with high profile stories on data breaches and even government accessing citizens’ personal information. The issues cited by State Chief Information Security Officers include unauthorized access to personal information, compliance with state statutes on privacy, and managing information sharing with third parties.
The state government can address the leading privacy concerns by aligning operational practices with the privacy policy.

